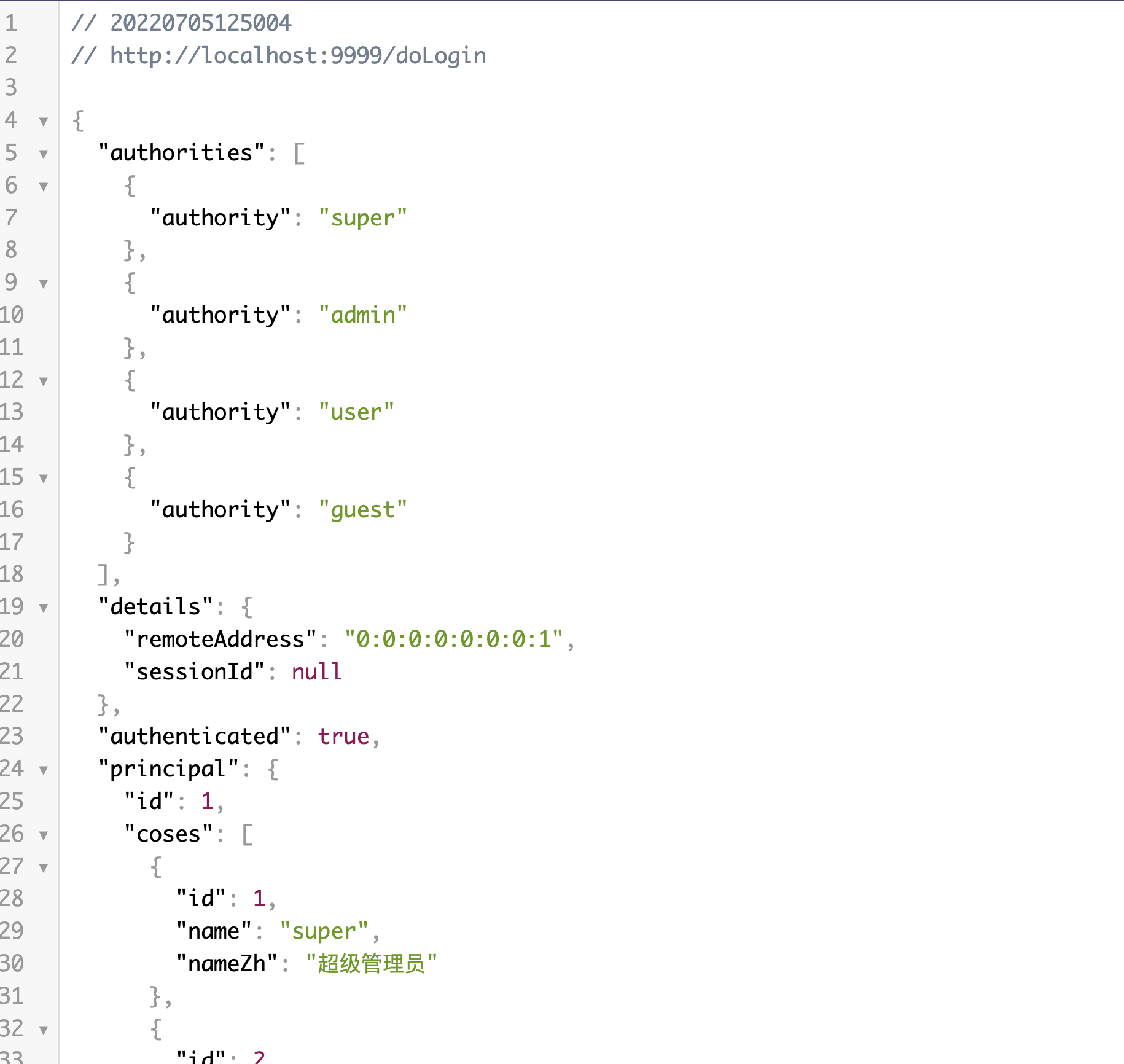
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
| create database if not exists springsecurityMybatis;
use springsecurityMybatis;
create table if not exists client(
`id` bigint NOT NULL AUTO_INCREMENT,
`name` varchar(255) DEFAULT NULL,
`phone`varchar(255) DEFAULT NULL,
`telephone`varchar(255) DEFAULT NULL,
`address`varchar(255) DEFAULT NULL,
`userface`varchar(255) DEFAULT NULL,
`remarks`varchar(255) DEFAULT NULL,
`account_non_expired` bit(1) NOT NULL DEFAULT 1,
`account_non_locked` bit(1) NOT NULL DEFAULT 1,
`credentials_non_expired` bit(1) NOT NULL DEFAULT 1,
`enable` bit(1) NOT NULL DEFAULT 1,
`password` varchar(255) DEFAULT NULL,
`username` varchar(255) DEFAULT NULL,
PRIMARY KEY (`id`)
)ENGINE=InnoDB DEFAULT CHARSET=utf8mb4 COLLATE=utf8mb4_0900_ai_ci;
create table if not exists cos(
`id` bigint NOT NULL AUTO_INCREMENT,
`name` varchar(255) DEFAULT NULL,
`name_zh` varchar(255) DEFAULT NULL,
PRIMARY KEY (`id`)
)ENGINE=InnoDB DEFAULT CHARSET=utf8mb4 COLLATE=utf8mb4_0900_ai_ci;
create table if not exists client_cos_relation(
`id` bigint NOT NULL AUTO_INCREMENT,
`client_id` bigint NOT NULL,
`cos_id` bigint NOT NULL ,
PRIMARY KEY (`id`)
)ENGINE=InnoDB DEFAULT CHARSET=utf8mb4 COLLATE=utf8mb4_0900_ai_ci;
insert into client_cos_relation (id,client_id,cos_id) values
(1,1,1),(2,1,2),(3,1,3),(4,1,4)
,(5,2,2),(6,2,3),(7,2,4)
,(8,3,3),(9,3,4)
,(10,4,4);
insert into client
(name, phone, telephone, address, userface, remarks, account_non_expired, account_non_locked, credentials_non_expired, enable, password, username)
values
('Benedict','123','020-123','Manchester','face1','haha',1,1,1,1,'111','Benedict')
,('本尼迪克特','123','021-123','曼彻斯特','face2','hehe',1,1,1,1,'111','本尼迪克特')
,('卷福','123','027-123','曼城','face3','呵呵',1,1,1,1,'111','卷福');
insert into cos (id, name, name_zh) VALUES (1, 'super','超级管理员'),(2,'admin','管理员'),(3,'user','普通用户'),(4,'guest','访客');
|